The world of network security is rife with threats, but one of the lesser-known yet highly effective methods hackers use to compromise a network is the ARP (Address Resolution Protocol) request and replay attack. This attack takes advantage of the vulnerabilities inherent in how devices communicate over local networks. In this story, we’ll explore what ARP is, how ARP request and replay attacks work, and how hackers leverage these tactics to hijack networks.
For a visual walkthrough of the concepts covered in this article, check out my YouTube Video:-
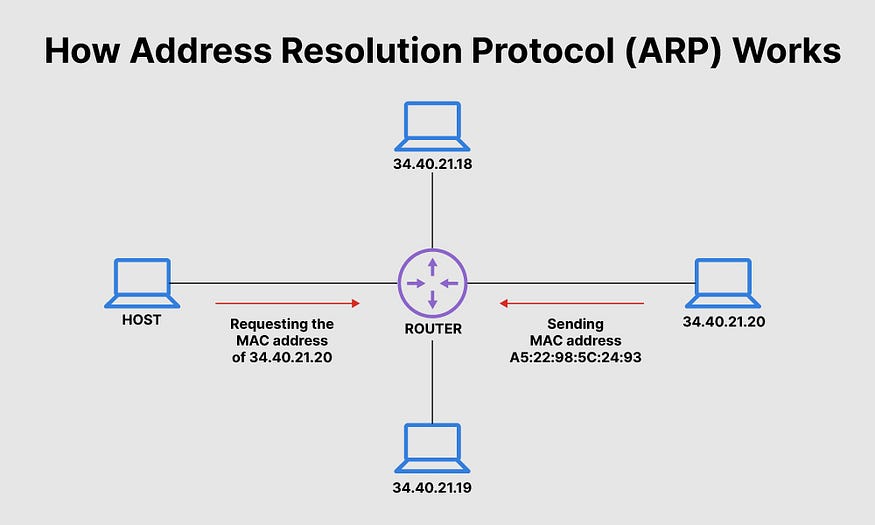
Understanding ARP: The Backbone of Local Network Communication
ARP is a protocol used within local area networks (LANs) to map IP addresses (logical addresses) to MAC addresses (physical hardware addresses). When a device wants to communicate with another device on the same network, it needs to know the MAC address of the target. Here’s how it works:
- The ARP Request: Device A sends an ARP request across the network asking, “Who has IP address X? Tell Device A.”
- The ARP Reply: The device with IP address X (Device B) responds with its MAC address, and Device A can now send data to Device B.
This process is efficient and happens behind the scenes to allow seamless communication between devices on the same network.
Exploiting ARP: Enter the ARP Request and Replay Attack
ARP, however, was not designed with security in mind. One of its greatest weaknesses is that it trusts every ARP reply it receives, regardless of whether it was actually requested or if the sender is legitimate. This lack of verification makes ARP susceptible to spoofing attacks.
In an ARP replay attack, a hacker listens to network traffic to intercept an ARP request, then sends their own (spoofed) ARP reply before the legitimate device can respond. This reply contains the hacker’s MAC address instead of the intended device’s MAC address. From that point forward, the data meant for the legitimate device is sent to the attacker’s machine.
Here’s a step-by-step breakdown of how the attack unfolds:
- Sniffing the Network: The attacker uses packet-sniffing tools to monitor ARP requests on the network.
- Intercepting the ARP Request: The attacker waits for a device (say, Device A) to send an ARP request, asking for the MAC address of another device (say, Device B).
- Injecting the ARP Reply: Before Device B can respond, the attacker quickly sends a spoofed ARP reply, pretending to be Device B but substituting their own MAC address.
- Hijacking Communication: Device A now sends all data meant for Device B to the attacker’s machine. The attacker can then read, modify, or drop the data, effectively hijacking the communication.
Amplifying the Threat: Replay Attack Variants
Replay attacks build upon the ARP spoofing technique. In a replay attack, the attacker not only intercepts and redirects traffic but also replays intercepted ARP requests or other network data at a later time, often to gain access to sensitive information.
For instance, after hijacking a session, an attacker could inject commands into a data stream between two devices, mimicking legitimate requests and responses. This type of attack is particularly dangerous in environments where authentication tokens or sessions are reused.
Consequences of ARP Attacks: Real-World Impact
ARP request and replay attacks can have devastating effects, especially in corporate environments where sensitive information is constantly flowing across the network. Once a hacker gains control of the traffic, they can:
- Eavesdrop on Sensitive Information: Attackers can capture login credentials, confidential files, and other sensitive data being transmitted over the network.
- Man-in-the-Middle (MitM) Attacks: By positioning themselves between two communicating devices, hackers can modify or inject malicious data, leading to potentially disastrous outcomes such as unauthorized access or malware installation.
- Network Disruption: In some cases, attackers can flood the network with spoofed ARP responses, causing legitimate devices to become confused and unable to communicate. This type of denial-of-service attack can cripple network functionality.
Defending Against ARP Request and Replay Attacks
While ARP attacks can be devastating, there are effective defenses that network administrators can implement to protect their infrastructure:
- Static ARP Entries: By manually configuring ARP entries on critical devices, you can prevent those devices from accepting unsolicited ARP replies. However, this method is only practical in smaller networks due to the administrative overhead.
- Use of Dynamic ARP Inspection (DAI): DAI is a security feature available in many modern network switches that verifies ARP packets based on DHCP snooping information. It ensures only valid ARP responses are forwarded, mitigating the risk of ARP spoofing.
- Encryption and Secure Protocols: Using encrypted protocols like HTTPS, SSH, and VPNs can protect the contents of communications, even if ARP attacks occur, by making the intercepted data unreadable to attackers.
- Network Monitoring: Tools like ARPwatch can alert administrators when suspicious ARP activity occurs, providing early warning signs of a potential ARP attack.
Conclusion: Stay Vigilant
ARP request and replay attacks expose the vulnerabilities in local network communication protocols, but with the right precautions, networks can be fortified against these threats. As hackers continuously seek new ways to exploit weaknesses, understanding the nature of ARP and its potential risks is critical for anyone responsible for network security.
By implementing proactive security measures like static ARP entries, dynamic ARP inspection, and encrypted communication protocols, network administrators can thwart ARP attacks and keep their systems safe from malicious hijackers. Stay vigilant, stay secure.
Connect with Me:
- YouTube ► S3 CloudHub Channel
- Facebook ► S3 CloudHub Page
- Medium ► S3 CloudHub Blog
- Demo Reference ► GitHub Repository
- Blog ► S3 CloudHub Blogspot
- Dev ► S3 CloudHub on Dev.to
- Free Udemy Courses ► Access Free Udemy Coupons

No comments:
Post a Comment