What is AWS Cloudformation?
AWS CloudFormation is an infrastructure as code (IaC) service that allows you to easily model, provision, and manage AWS and third-party resources.
What is AWS Security Hub?
- AWS Security Hub provides you with a comprehensive view of your security state in AWS and helps you check your environment against security industry standards and best practices.
- Security Hub collects security data from across AWS accounts, services, and supported third-party partner products and helps you analyze your security trends and identify the highest priority security issues.
Benefits of AWS Security Hub
- Security Hub reduces the effort to collect and prioritize security findings across accounts from integrated AWS services and AWS partner products.
- Security Hub automatically runs continuous, account-level configuration and security checks based on AWS best practices and industry standards.
- Security Hub consolidates your security findings across accounts and provider products and displays results on the Security Hub console.
Declare a Hub Resource Using Cloudformation
The AWS::SecurityHub::Hub resource represents the implementation of the AWS Security Hub service in your account. One hub resource is created for each Region in which you enable Security Hub.
The CIS AWS Foundations Benchmark standard and the Foundational Security Best Practices standard are also enabled in each Region where you enable Security Hub.
Steps to create resources in cloudformation
Search Cloudformation in aws console

Create a new Stack
A stack is a collection of AWS resources that you can manage as a single unit. All the resources in a stack are defined by the stack’s AWS CloudFormation template
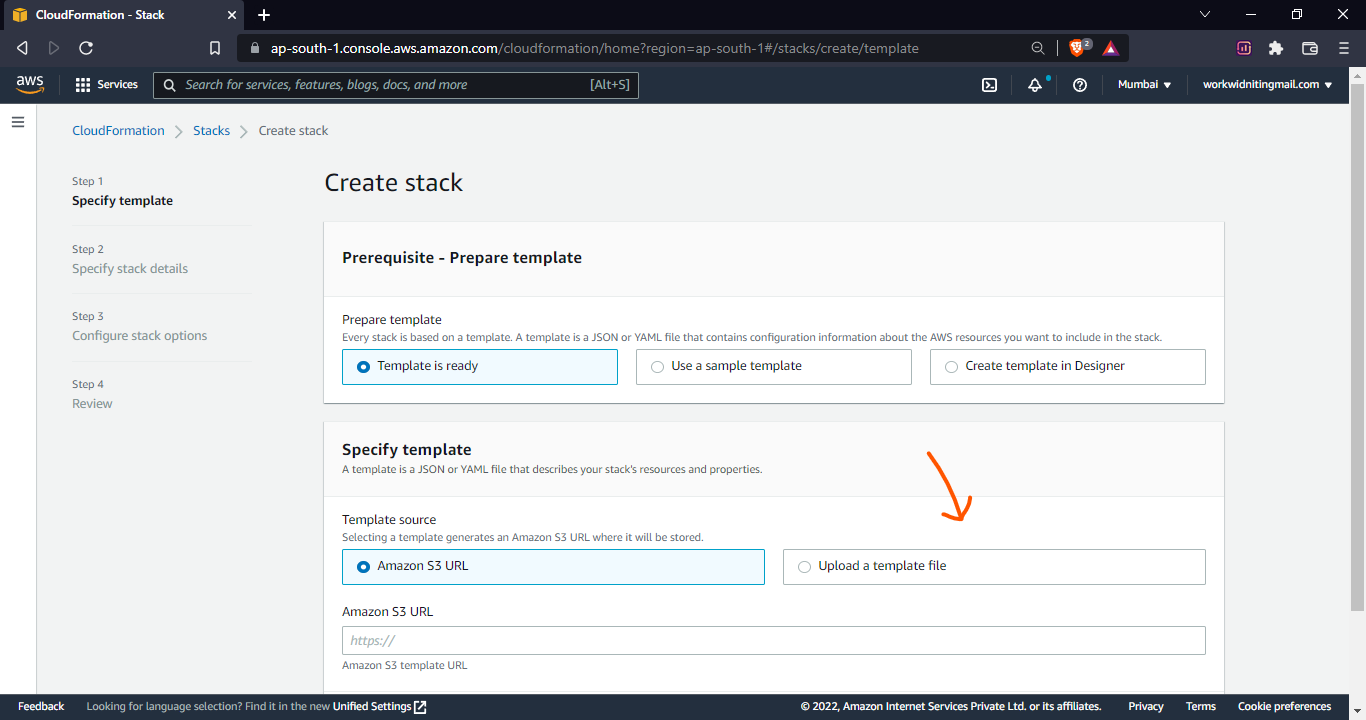
Save the below code in .yaml format & then upload a file after that click next.
Description: Example Hub with Tags
Parameters:
Tags:
Type: String
Resources:
ExampleHubWithTags:
Type: 'AWS::SecurityHub::Hub'
Properties:
Tags:
key1: value1
key2: value2
Outputs:
HubArn:
Value: !Ref ExampleHubWithTags
Give the Name of the stack and define the parameter.

Again click next

Now Review your stack and then click Create Stack

Now creating a stack

Now your Stack is successfully created

Using this stapes, you can also create sagemaker pipeline using cloudformation.
The AWS::SageMaker::Pipeline resource creates shell scripts that run when you create and/or start a SageMaker Pipeline. For information about SageMaker Pipelines, see SageMaker Pipelines in the Amazon SageMaker Developer Guide.
Use the below code to create sagemaker pipeline
Parameters:
PipelineName:
Description: The name of the pipeline.
Type: String
Default: "mypipe"
PipelineDisplayName:
Description: The display name of the pipeline.
Type: String
Default: "mydisplay"
PipelineDescription:
Description: The description of the pipeline.
Type: String
Default: "mydiscription"
PipelineDefinitionBody:
Description: The definition of the pipeline. This can be either a JSON string or an Amazon S3 location.
Type: String
Default: "{\"Version\":\"2020-12-01\",\"Parameters\":[{\"Name\":\"InputDataSource\",\"DefaultValue\":\"\"},{\"Name\":\"InstanceCount\",\"Type\":\"Integer\",\"DefaultValue\":1}],\"Steps\":[{\"Name\":\"Training1\",\"Type\":\"Training\",\"Arguments\":{\"InputDataConfig\":[{\"DataSource\":{\"S3DataSource\":{\"S3Uri\":{\"Get\":\"Parameters.InputDataSource\"}}}}],\"OutputDataConfig\":{\"S3OutputPath\":\"s3://my-s3-bucket/\"},\"ResourceConfig\":{\"InstanceType\":\"ml.m5.large\",\"InstanceCount\":{\"Get\":\"Parameters.InstanceCount\"},\"VolumeSizeInGB\":1024}}}]}"
RoleArn:
Description: The Amazon Resource Name (ARN) of the IAM role used to execute the pipeline.
Type: String
Default: "arn:aws:iam::293328213636:role/sagemaker_custom"
Resources:
MyAwesomePipeline:
Type: AWS::SageMaker::Pipeline
Properties:
PipelineName:
Ref: PipelineName
PipelineDisplayName:
Ref: PipelineDisplayName
PipelineDescription:
Ref: PipelineDescription
PipelineDefinition:
PipelineDefinitionBody:
Ref: PipelineDefinitionBody
RoleArn:
Ref: RoleArn
Outputs:
PipelineName:
Description: Name of pipeline
Value:
Ref: MyAwesomePipeline

No comments:
Post a Comment